Podman
A Brief Overview of Podman
Containerization
Linux Namespace
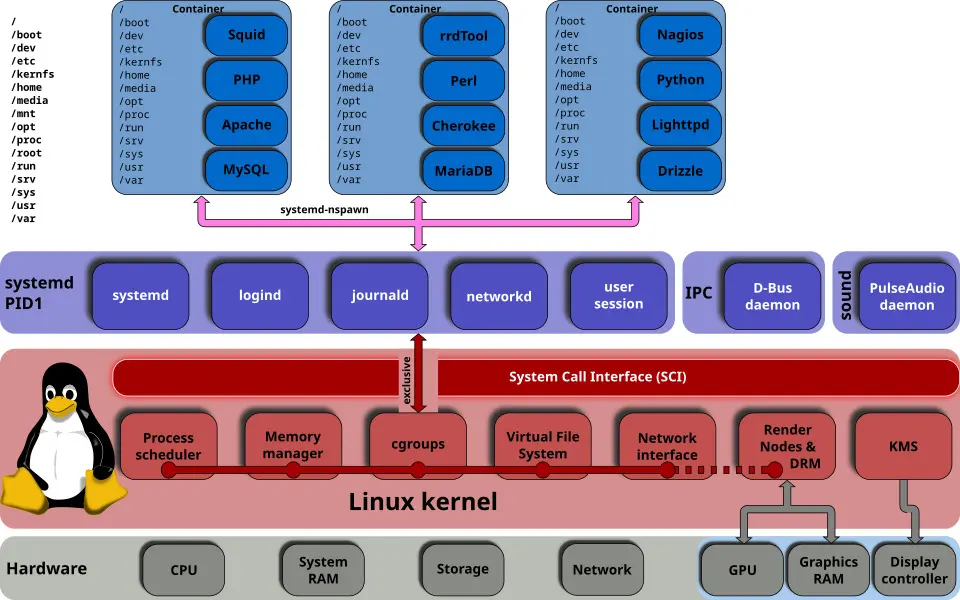
Docker
Docker is an incredibly convenient and largely foolproof solution for implementing operating-system-level virtualization in the manner of streamlined packages (containers).
By its nature, production environments rely upon fully packaged images with base sub-systems (e.g., Alpine/Bottlerocket/Ubuntu)—to bypass environmental complexity.
Developers and system maintainers may simply deploy an immutable image, ensuring interoperability concerns are adequately addressed.
No dependency hell, no version mismatch, and no cross-platform interference.Typical Deployment Pattern:
- A Unix-like host provides OS-level virtualization.
- Ansible playbook/Docker compose YMLs are configured.
- Containers are mediated/deployed via a web console.
- Often run as root, only application/container-specific variables are addressed.
1### Example Ansible Playbook ###
2# ! Via docs.ansible.com ! #
3- name: Update web servers
4 hosts: webservers
5 remote_user: root
6
7 tasks:
8 - name: Ensure apache is at the latest version
9 ansible.builtin.yum:
10 name: httpd
11 state: latest
12
13 - name: Write the apache config file
14 ansible.builtin.template:
15 src: /srv/httpd.j2
16 dest: /etc/httpd.conf
17
18- name: Update db servers
19 hosts: databases
20 remote_user: root
21
22 tasks:
23 - name: Ensure postgresql is at the latest version
24 ansible.builtin.yum:
25 name: postgresql
26 state: latest
27
28 - name: Ensure that postgresql is started
29 ansible.builtin.service:
30 name: postgresql
31 state: startedCaveats
Ironically, in common production environments, Docker configuration is often left unchanged—ignorantly left running as root.
When left misconfigured, a containerized root environment can correspond to the host’s underlying root user.
In a rootful state, it presents a massive, glaringly obvious increase in post-exploit severity.
Rootful containers will map to UID 0.